Inside the NETGEAR WNAP320: Exploring Firmware Emulation Techniques
My research began by studying how router firmware can be emulated in two popular ways.
- With The Firmware Analysis Toolkit
- Using Firmadyne
Fusing Firmware Analysis Toolkit
Starting our adventure into emulator router firmware, we have Firmware Analysis Toolkit (FAT). This is a complete toolkit that includes firmware image analysis and bin images.
Tools You Will Need
What you will need beforehand:
- Ubuntu: The Firmware Analysis Toolkit runs from the command line on a Linux environment, and Ubuntu is an easy-to-use option.
- Firmware Analysis Toolkit: Tool for analyzing (x86) firmware. You can download it from here. With this powerful toolkit, you would be able to effortlessly analyze and emulate firmware images.
- Firmware File: Netgear WNAP320 Firmware.
Setting Things Up
1. Prerequisites
Ensure that all the dependencies are installed before downloading the Firmware Analysis Toolkit. Copy these commands into your terminal:
sudo apt-get update
sudo apt-get install git python3 python3-pip python3-dev
2. Clone the Firmware Analysis Toolkit
If you do not already have GIT installed, download it! Clone the Firmware Analysis Toolkit repository onto your local machine using Git:
git clone https://github.com/attify/firmware-analysis-toolkit.git
cd firmware-analysis-toolkit
3. Install the Binwalk Dependencies
Run the following commands to install the necessary dependencies and tools:
cd firmware-analysis-toolkit/binwalk
sudo ./deps.sh
sudo python setup.py install
4. Download the Firmware
Get a firmware image for your NETGEAR WNAP320 device. This is usually available on the manufacturer's support website.
5. Emulating Firmware Image
Run the following command to emulate the firmware image:
sudo ./fat.py WNAP320\ Firmware\ Version\ 2.0.3.zip
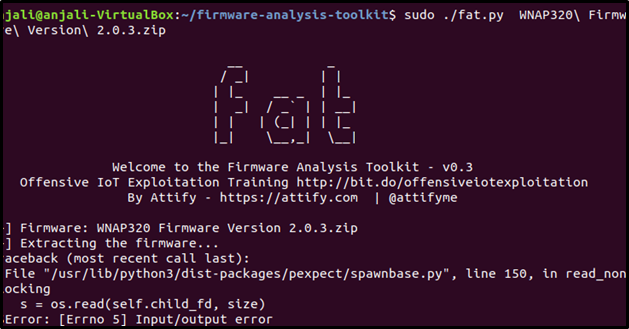
Above could be the error you could get. Don't worry, u can go with method no. 2
Emulating Firmware with Firmadyne
Firmadyne
Another very useful tool for firmware emulation, Firmadyne is designed specifically to automatically extract, configure, and emulate firmware within a controlled system. It makes it easier to analyze firmware behavior, provides flexibility, and lets you observe the intricate details surrounding vulnerabilities.
Tools You Will Require
You will need to have the following items before you get started:
- Ubuntu (Version 18 or 22): Like the Firmware Analysis Toolkit, Firmadyne runs better on Linux-based OS like Ubuntu.
- Firmadyne: Download Firmadyne from here.
- Firmware Image: The firmware you want to emulate. For this setup, we will use the NETGEAR WNAP320 firmware.
Setting Things Up
1. Install Prerequisites
First, install all the required tools and dependencies that Firmadyne needs:
sudo apt install busybox-static fakeroot git dmsetup kpartx netcat-openbsd nmap python3-psycopg2 snmp uml-utilities util-linux vlan python3-pip python3-magic
2. Make Python 3 Default
Some systems come with Python 2 pre-installed, so you may want to set Python 3 as the default interpreter:
sudo update-alternatives --install /usr/bin/python python /usr/bin/python3 10
3. Clone The Firmadyne Repository
Clone the Firmadyne repository from GitHub:
git clone --recursive https://github.com/firmadyne/firmadyne.git
4. Clone Binwalk
git clone https://github.com/ReFirmLabs/binwalk.git
5. Install Binwalk Dependencies
cd binwalk
sudo ./deps.sh
sudo python ./setup.py install
6. Install PostgreSQL
Firmadyne uses PostgreSQL for storing firmware data. Install and initialize the database:
sudo apt install postgresql
sudo -u postgres createuser -P firmadyne
(Enter password for 'firmadyne' user)
sudo -u postgres createdb -O firmadyne firmware
sudo -u postgres psql -d firmware < ./firmadyne/database/schema
7. Fetch More Firmadyne Resources
cd firmadyne
./download.sh
8. QEMU Installation
Install QEMU along with the required architectures and utilities:
sudo apt install qemu-system-arm qemu-system-mips qemu-system-x86 qemu-utils
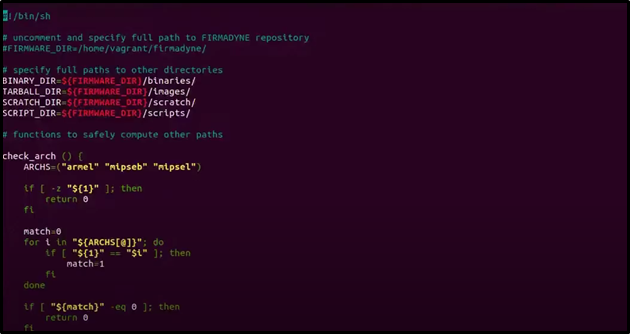
9. Edit Firmadyne Configuration
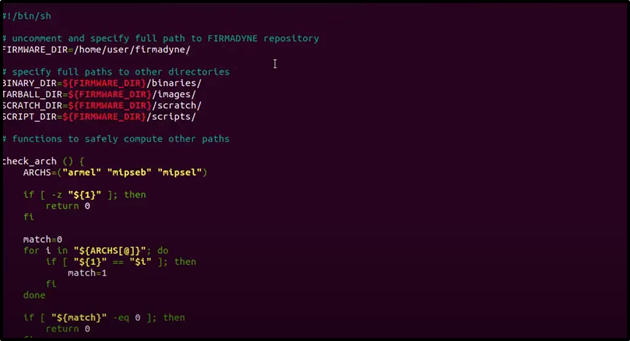
10. Extracting The Firmware
Extract the NETGEAR firmware using Firmadyne's extractor tool:
python3 ./sources/extractor/extractor.py -b Netgear -sql 127.0.0.1 -np --nk "$ZIP_FILE" images
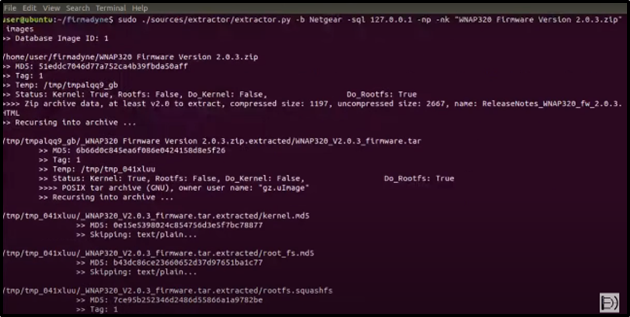
Confirm that the firmware was extracted successfully:
ls images
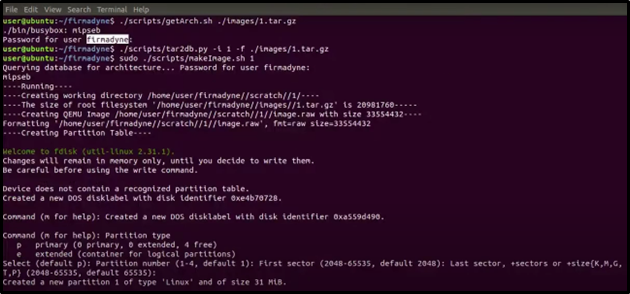
11. Get Firmware Architecture
Run the following command to determine the firmware architecture:
./scripts/getArch.sh ./images/1.tar.gz
12. Upload the Firmware to the Database
./scripts/tar2db.py -i 1 -f ./images/1.tar.gz
13. Create the Emulation Image
sudo ./scripts/makeImage.sh 1
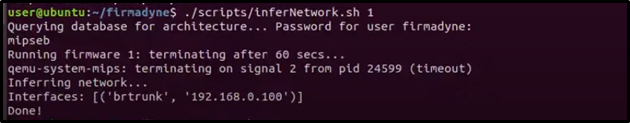
14. Infer the Network Configuration
./scripts/inferNetwork.sh 1
15. List Emulated Files
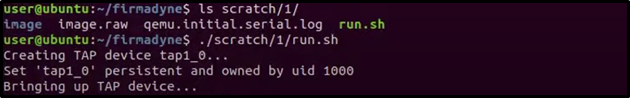
ls scratch/1/
16. Run the Emulation
Execute the firmware in the emulated environment:
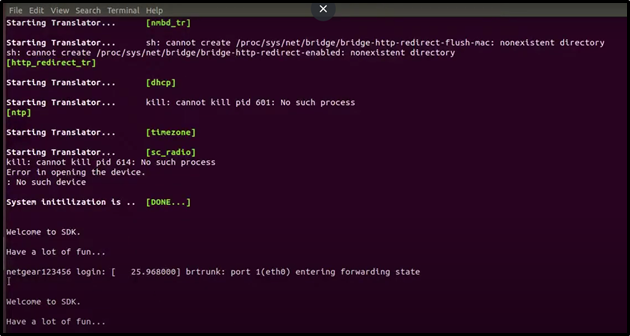
./scratch/1/run.sh
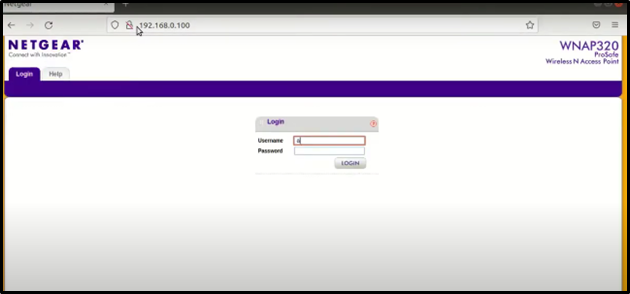
Credentials:
USERNAME: admin
PASSWORD: password
FINALLY!!! EMULATION IS DONE!!
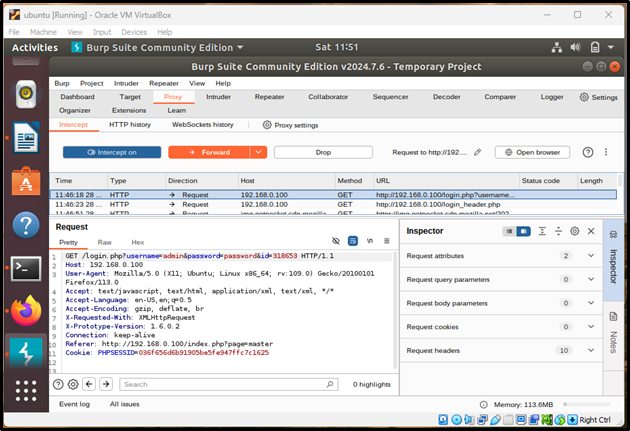
17. Intercepting Traffic on Burp Suite
After emulation, set a proxy in Firefox and intercept traffic using Burp Suite.