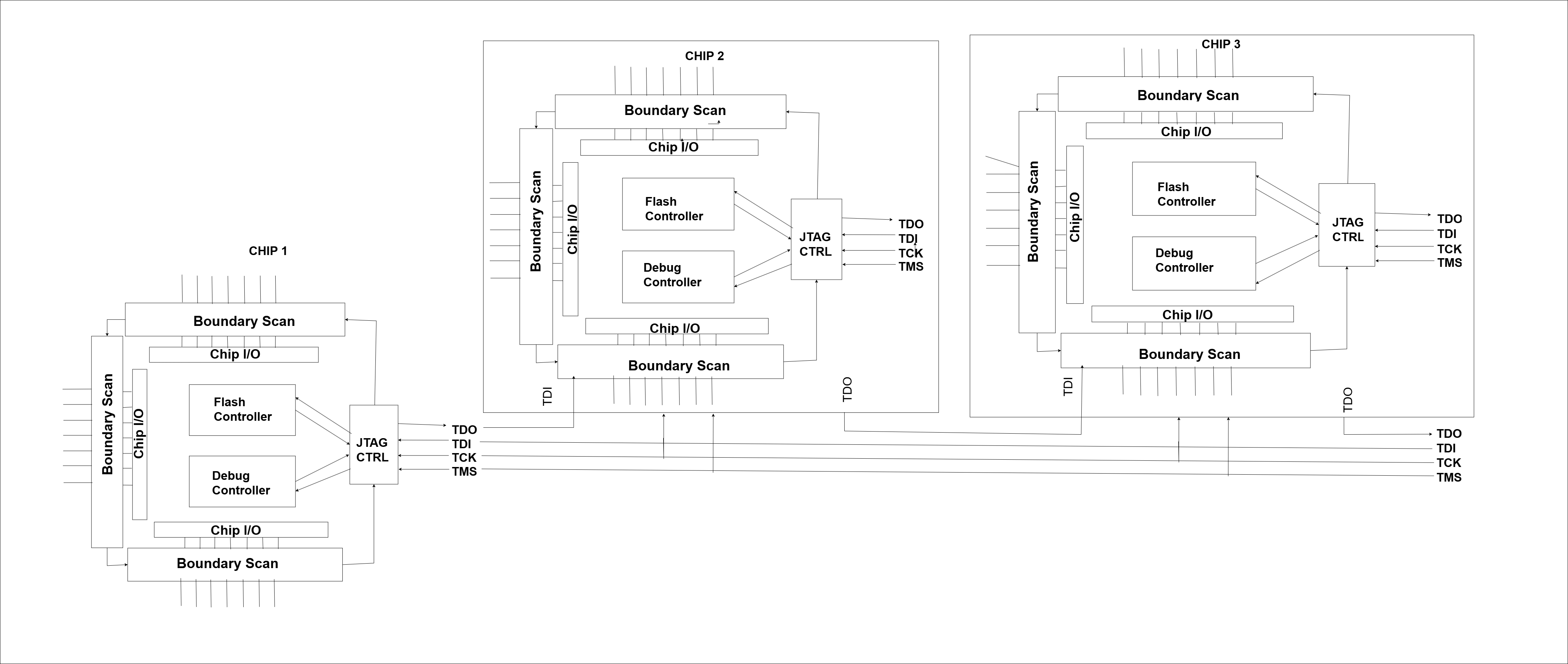
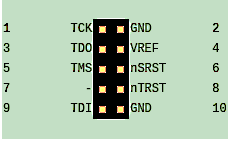JTAG is often referred to as Boundary Scan Testing because one of its primary uses is testing connections on a chip or PCB without needing direct physical access to internal circuitry.
JTAG operates through a serial communication interface that uses a specific set of pins:
JTAG Pin Functions
- TDI (Test Data In): Sends data into the device.
- TDO (Test Data Out): Outputs data from the device.
- TMS (Test Mode Select): Controls the state transitions of the JTAG state machine.
- TCK (Test Clock): Provides the clock signal for synchronizing data transfer.
- TRST (Test Reset): An optional pin used to reset the test logic.
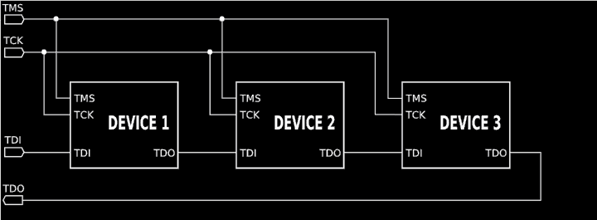
The boundary scan cells are small logic elements inserted between a chip's core logic and its input/output (I/O) pins. Think of them as checkpoints placed right at the edge (or boundary) of the chip. These cells form a scan chain a single line of serial data that flows through each cell and out to the other end.
When the chip powers on, boundary scan logic stays passive and allows signals to pass normally between the core and the I/O. But when JTAG is activated, it can take control of these cells, shifting test data in and out using the scan chain.
Board Testing
Test board level interconnects and diagnose faulty solder joints or broken traces.
Signal Validation
Validate signal paths without needing probes or oscilloscopes.
In short, boundary scan turns your chip into its own testing tool very handy when you're dealing with dense PCBs or tightly packed BGA components.