Most people associate the term hacking with three things which include password theft and Instagram account breaches and laptop malware attacks. That mental model completely breaks when you move into satellites.
Satellite hacking isn't about breaking into a website. It's about controlling a machine that you can't physically touch, can't reboot manually, and can't fix once something goes wrong.
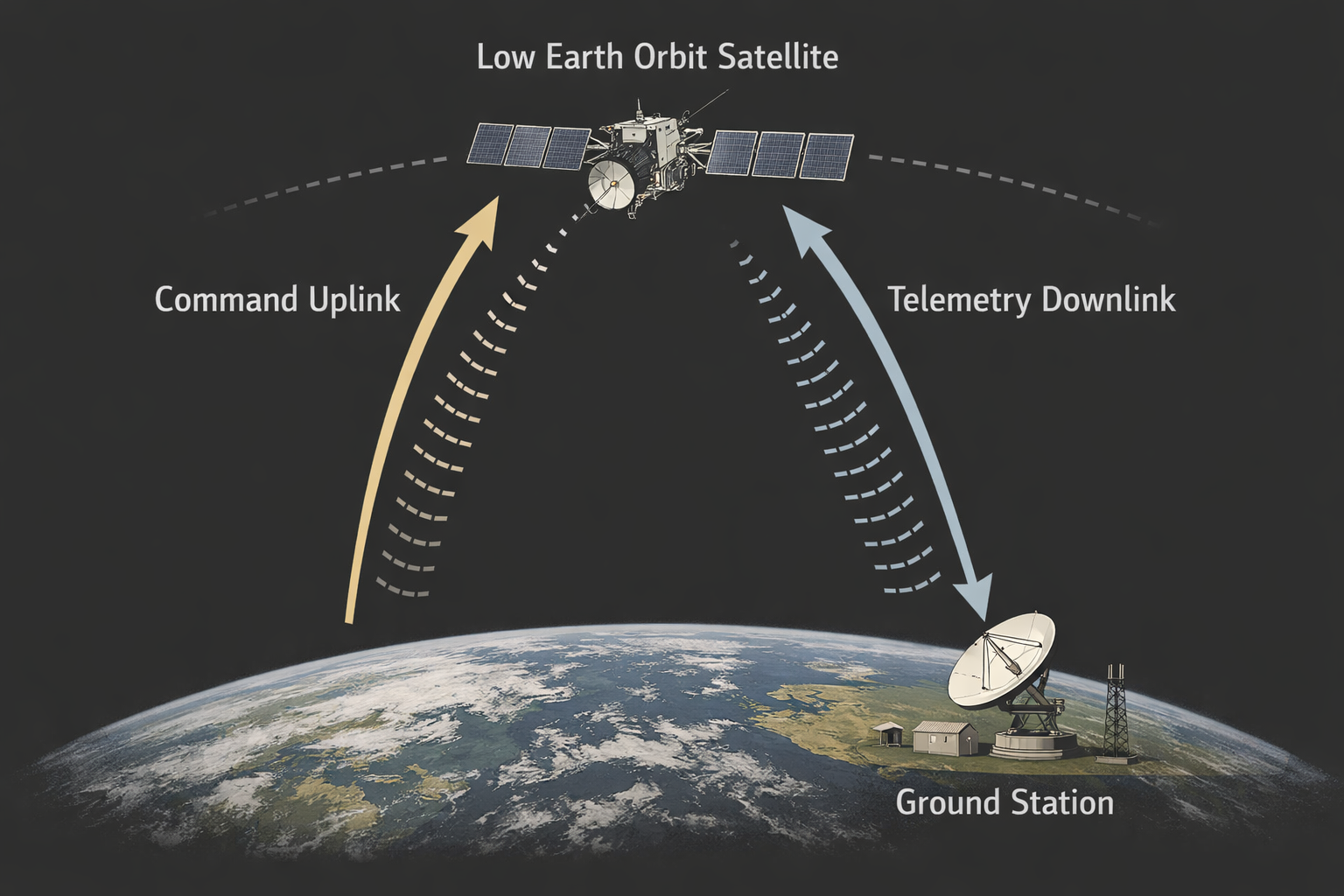
A satellite travels around the Earth at extreme velocities and its operations depend entirely on software control. If that software is abused, the satellite will happily follow along.

In practice, hacking a satellite usually means one of these things:
In practice, hacking a satellite means:
- Sending commands you were never supposed to send
- Faking or manipulating telemetry data
- Crashing the onboard computer
- Locking out the real operators permanently
There's no "factory reset" in orbit.
That's what makes this field high-risk and high-impact.

