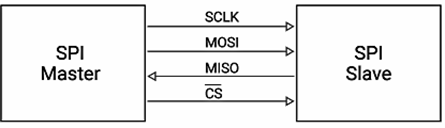
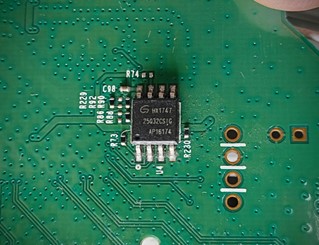
This blog series is focused on SPI hacking with practical application in hardware analysis, firmware extraction, and embedded device inspection. Understanding this protocol is essential before moving on to hands-on tools and extraction techniques, which will be discussed in upcoming parts.
This post is for the curious: makers, tinkerers, and hackers who want to understand what SPI is, how it works, and why it matters in real-world hardware hacking. We'll cover everything from the basics of the protocol to how it plays into accessing flash memory chips. Whether you're trying to dump a router's firmware or dig into an old motherboard.